The Forefront UAG DirectAccess deployment guide covers the planning and configuration in great detail. What isn’t discussed in depth is the deployment of certificates. Any UAG computers that offers DirectAccess services must have an IP-HTTS and IPSec certificate. In addition, the network location server requires a SSL certificate for server authentication. Depending on your public key infrastructure (PKI) it might be necessary to deploy the server certificates manually. This post is about creating and enrolling the required certificates manually.
Note: It is assumed that an operational PKI is already available.
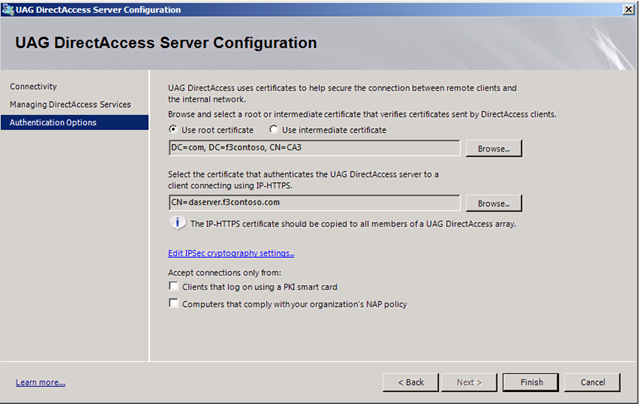
The Authentication Options dialog
To finalize the Authentication Options dialog you must have three certificates available: The root certification authority (CA), the IP-HTTPS certificate and the computer’s IPSec authentication certificate.
Assigning the root certification authority
When configuring the Authentication Options for the DirectAccess server, you must set the root CA certificate where client certificates are verified against. Every computer that should be DirectAccess enabled requires a valid certificate which can be used for client authentication. The root CA certificate configured in the Authentication Options must be the topmost parent in the certificate chain of the client certificates.
In case you are using an Enterprise CA in your Active Directory environment, the root CA certificate is usually deployed automatically through group policies to all computers in the forest. However, if you cannot find the root CA certificate you should verify your PKI configuration or publish the root CA certificate manually with the following command:
certutil –dspublish RootCAfile.cer RootCA
If the root CA certificate is available to the UAG server, select it through the Browse dialog.
Providing the IP-HTTPS certificate
The IP-HTTPS certificate must be installed locally on the UAG server to be assigned in the Authentication Options dialog. The certificate enrollment process breaks down into 4 steps:
1. Creating an INF file to set the certificate properties
Use Notepad to create the INF file with the template below. The text marked in red must be changed according to your configuration. Safe the file as IP-HTTPS.inf
[Version]
Signature="$Windows NT$"
[NewRequest]
Subject = "CN=DASERVER.CONTOSO.COM" ; Replace the subject name with the FQDN of your UAG server
Exportable = FALSE ; Private key is not exportable
KeyLength = 2048 ; Common key sizes: 512, 1024, 2048, 4096, 8192, 16384
KeySpec = 1 ; AT_KEYEXCHANGE
KeyUsage = 0xA0 ; Digital Signature, Key Encipherment
MachineKeySet = True ; The key belongs to the local computer account
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
ProviderType = 12
SMIME = FALSE
RequestType = CMC
[Strings]
szOID_ENHANCED_KEY_USAGE = "2.5.29.37"
szOID_PKIX_KP_SERVER_AUTH = "1.3.6.1.5.5.7.3.1"
[Extensions]
%szOID_ENHANCED_KEY_USAGE% = "{text}%szOID_PKIX_KP_SERVER_AUTH%"
[RequestAttributes]
CertificateTemplate = WebServer
2. Compiling the INF file into a REQ file
The following command-line command will generate key material and turn the INF file into a certificate request.
certreq –new IP-HTTPS.inf IP-HTTPS.req
Once the certificate request was created you can verify the request with the following command:
certutil IP-HTTPS.req
3. Submitting the REQ file to the CA
Usually, a locally generated certificate can be submitted to a remote CA. However, if UAG is installed on a computer, the TMG policies prohibit the RPC communication with the CA. If you try to submit the REQ file from UAG to the CA you will receive the following error message: “The RPC server is unavailable. 0x800706ba (WIN32: 1722)”. Therefore, you must transfer the REQ file from the UAG to the CA or at least a computer that can access the CA directly.
To submit the certificate request to the CA, perform the following command:
certreq –submit IP-HTTPS.req
Depending on the CA configuration, the certificate is enrolled immediately and you can store it to a file as IP-HTTPS.cer.
4. Installing the certificate on the UAG computer and assigning it to the UAG configuration
The file containing the IP-HTTPS certificate must be transferred back to the UAG computer. To install and link the certificate with the private key material run the following command on the UAG computer:
certreq –accept IP-HTTPS.cer
Once the certificate was installed, it can be selected from the Browse… dialog.
Providing the IPSec authentication certificate
At this stage, the UAG computer might not have an IPSec certificate and you will see the following warning at the bottom of the Authentication Options dialog:
Enrolling for an IPSec certificate manually is very similar to the enrollment process of the IP-HTTPS certificate. What differs is the creation of the INF file. The steps 2 to 4 as described above are similar however you should use a different file name for the INF, REQ and CER file generated.
The INF file for the IPsec certificate should look like the following template. The text marked in red must be changed according to your configuration. Use Notepad to create the INF file.
[Version]
Signature="$Windows NT$"
[NewRequest]
Exportable = FALSE ; Private key is not exportable
KeyLength = 2048 ; Common key sizes: 512, 1024, 2048, 4096, 8192, 16384
KeySpec = 1 ; AT_KEYEXCHANGE
KeyUsage = 0xA0 ; Digital Signature, Key Encipherment
MachineKeySet = True ; The key belongs to the local computer account
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
ProviderType = 12
SMIME = FALSE
RequestType = CMC
[Strings]
szOID_SUBJECT_ALT_NAME2 = "2.5.29.17"
szOID_ENHANCED_KEY_USAGE = "2.5.29.37"
szOID_PKIX_KP_CLIENT_AUTH = "1.3.6.1.5.5.7.3.2"
[Extensions]
%szOID_SUBJECT_ALT_NAME2% = "{text}dns=hostname.contoso.com" ; set the FQDN of the UAG computer here!
%szOID_ENHANCED_KEY_USAGE% = "{text}%szOID_PKIX_KP_CLIENT_AUTH%"
Once the file is saved to the UAG computer, apply steps 2 to 4 from the above section. Once the IPsec certificate was installed on the UAG computer, the warning message will go away and the Authentication Options dialog can be finished.
Enrolling for the network location server certificate
The network location server requires a standard SSL certificate. You can enroll for the certificate on the network location server either from the IIS certificate enrollment wizard or create the certificate request manually according to the steps described above.
For manual certificate request processing you can use the INF file template in the IPSec section above. The only change that must be made to the template is the subject alternate name (marked in red). The subject alternate name must be equal to the name that is configured as network location server in the Infrastructure Server Configuration dialog in UAG.



Nice article and you are right! I could\’nt find anything out there about the right way to request certs for directaccess. I am running into a problem with the IPSEC certificate request. it would appear that I dont have that template in my ca. I can duplicate and enable one but I am not sure on how I should be configuring the template. Could you point me in the right direction?I am getting:The request contains no certificate template information. 0x80094801
Same Issue here, everything works as documented until I hit the template error. Have you had any luck resolving this?
Just a quick FYI for those comments about a certificate template. After you have duplicated and enabled the template you can request that template type with CertificateTemplate = <TemplateCopyNameWithNOSpaces>. It was a lucky guess when I was running into these issues. But if you don\’t like luck you can use the following commands to list the template types: certuilt -CATemplates